In the rapidly advancing domain of cloud computing, ensuring the resilience and security of business-critical applications and data against sophisticated cyber threats has become imperative for organizations worldwide. Ransomware attacks have become a significant threat to enterprises, challenging the security and resilience of cloud environments. Traditional defense mechanisms, while essential, are not always sufficient to prevent sophisticated cyber threats. In response to this evolving landscape, Appranix has developed a comprehensive cloud resilience model that emphasizes not just defense but robust recovery and rebuilding capabilities. This approach ensures that businesses can swiftly recover from ransomware attacks, minimizing downtime and data loss. This blog post highlights how Appranix leverages data immutability, air-gapping, zero-trust architectures, and automated recovery processes to rebuild and fortify cloud environments post-ransomware attacks.

The Essence of Cloud Resilience
cloud resilience is the ability of cloud services, applications, and critical data to withstand and rapidly recover from disruptions, ensuring uninterrupted operation and data integrity. This concept extends beyond mere disaster recovery, encapsulating proactive measures that prevent downtime and data loss while enhancing security and compliance. Appranix's model elevates cloud resilience, leveraging cloud-native services and methodologies to protect against both current and emerging threats.
-
Immutability: The Bedrock of Resilience
At the core of Appranix's strategy is data and configuration immutability. Immutability ensures that once data or configurations are set, they cannot be altered or tampered with, thereby safeguarding against unauthorized changes and cyber attacks.
-
Air-Gapping: Virtual Fortification
Traditionally, air-gapping meant physically isolating a network from the internet to secure it against unauthorized access. Appranix has innovatively adapted this concept for the cloud, creating virtually air-gapped environments that isolate critical data and applications from potential threats. This virtual separation effectively minimizes the attack surface, offering an additional layer of security and significantly bolstering cloud resilience.
-
Zero-Trust: A Paradigm Shift in Security
Appranix's resilience model is deeply rooted in the zero-trust security framework, which operates on the principle that no entity should be trusted by default, regardless of its location or relationship with the organization. By implementing strict access controls and continuously verifying every access request, Appranix ensures that only authorized personnel can access critical data, thereby preventing data breaches and enhancing the overall security posture.
The Appranix Difference: A Comprehensive Approach to Cloud Resilience
What sets Appranix apart is its holistic approach to cloud resilience, meticulously designed to address the multifaceted challenges of application rebuilds from clean golden copies:
Appranix offers a robust suite of protections designed to ensure the highest levels of security and resilience for your cloud application environments and critical data. Our approach is tailored to meet diverse requirements and maturity levels, providing peace of mind through multiple layers of immutability and air-gapped protection.
-
Cloud Configuration Immutability
At the foundation, our Dual-vault Cloud Time Machine secures cloud configurations in an external cloud account. This separation is fortified with 256-bit encryption and adheres to rigorous SOC 2 controls, ensuring that your configurations remain immutable, isolated, and protected from unauthorized access.
-
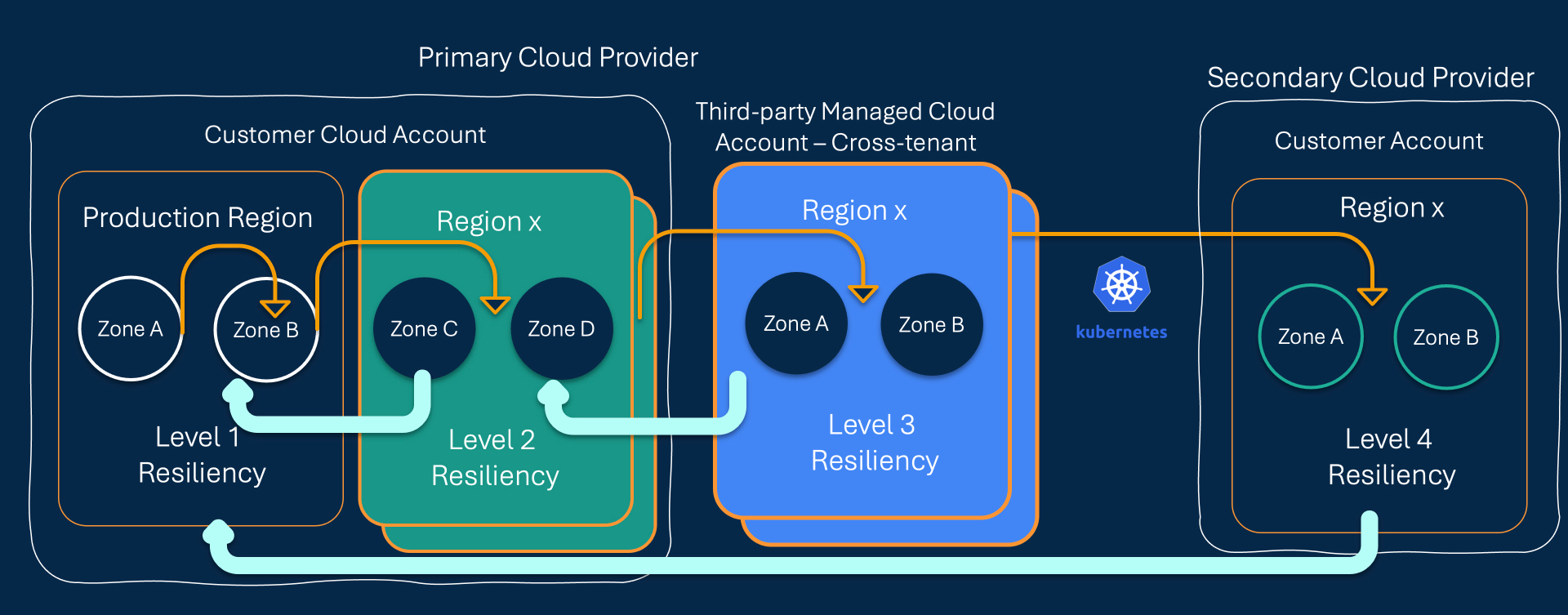
Application Data Immutability - Level 1
Our snapshot-based data protection strategy guarantees the immutability of your application data. By creating unmodifiable snapshots, we ensure that data cannot be altered unless it is purposefully restored, maintaining its integrity without extracting data from your environment.
-
Application Data Immutability - Level 2 with Air-Gapped Network
Enhancing protection, Appranix replicates application data to a separate cloud region within an air-gapped Virtual Private Cloud (VPC). This layer not only preserves data immutability but also significantly reduces the risk of unauthorized access.
-
Application Data Immutability - Level 3 with Zero-trust and Air-Gapped Network
Elevating security measures, we offer replication to an entirely isolated AWS cloud account. This account is air-gapped and accessible only to authorized personnel under a zero-trust framework, where permissions are dynamically allocated and revoked, ensuring unparalleled data protection.
When Appranix validates the snapshots with fingerprints from the original production environments to make sure only the verified snapshots are recoverable for the application rebuilds.
-
Application Data Immutability - Level 4 with Zero-trust and Air-Gapped Cross-Cloud Network
For fully containerized applications, Appranix extends its capabilities to cross-cloud protection. We can migrate your application environment and data to a different hyperscale provider, achieving complete isolation from the production cloud network, underpinned by a zero-trust and air-gapped architecture.
-
Why automated recovery testing is still important?
Beyond these protective measures, Appranix integrates policy-based automated recovery and reporting capabilities. This allows for human-free recovery testing and comprehensive reporting, further enhancing your resilience against potential disruptions.
Conclusion
As cloud computing continues to evolve, the need for innovative cloud resilience strategies becomes increasingly critical. Appranix's pioneering cloud resilience model offers a forward-thinking solution. With its unique blend of immutability, air-gapping, and zero-trust architectures, Appranix empowers organizations to navigate the digital landscape with assurance, ensuring their cloud environments are not only secure but truly resilient with rebuild capabilities. Let’s move beyond the traditional data backup and disaster recovery models towards a holistic cloud resilience model.
